
Access Control Lists (ACLs) plays a crucial role in managing permissions and enhancing security in a Linux environment. Access Control Lists (ACLs) is a powerful mechanism that enhances the traditional file and directory permissions. They provide a way to grant or deny specific permissions to users or groups beyond the basic owner-group-others model. As a Linux enthusiast, exploring ACLs has enlightened me, offering granular control over file and directory access.
Earlier, the only individuals requiring access to Linux filesystems could be broadly categorized through the lens of traditional Linux file system permissions. In those simpler days, access control was delineated primarily among users, groups, and others, with read, write, and execute privileges serving as the limited spectrum of access rights. Finally, growing demands for precise file access led to a new era with Access Control Lists offering detailed permissions. ACLs enable precise permission customization, offering a sophisticated and adaptable approach to managing access in Linux environments. This marked the beginning of a transformative journey from the simplicity of standard permissions to the versatility and precision offered by ACLs. However this added granularity empowers administrators to fine-tune access control, ensuring that specific users or groups have tailored permissions on a file or directory.
Modifying Specific ACL Entries
Syntax:
//For user;
setfacl -m u:username:permissions <file_or_directory>
//For Group;
setfacl -m g:groupname:permissions <file_or_directory>Example:
setfacl -m u:username:rw /path/to/fileLet me share a real time example; In a company where the Sales and Finance departments often collaborated on shared data.
In the shared directory /company/shared, the Sales and Finance departments needed different levels of access to files. The Sales team required read and write access for collaboration, while the Finance team needed read-only access to maintain data integrity.
Before configuring ACLs, make sure to install the acl package using your package manager:
[root@ervintest ~]# yum install -y acl Set Default ACLs:
Grant read and write permissions to Sales group, read-only to Finance group
[root@ervintest ~]# setfacl -m g:sales:rwx /company/shared
[root@ervintest ~]# setfacl -m g:finance:rx /company/shared
Sales should have read and write permission to a file sales_report.xlsx in shared directory. Then finance should have read only permission for financial_summary.pdf in the shared directory.
For this specific files, customize ACLs based on department needs:
[root@ervintest ~]# setfacl -m g:sales:rw /company/shared/sales_report.xlsx
[root@ervintest ~]# setfacl -m g:finance:r /company/shared/financial_summary.pdf
To confirm the intended ACLs
[root@ervintest ~]# getfacl /company/shared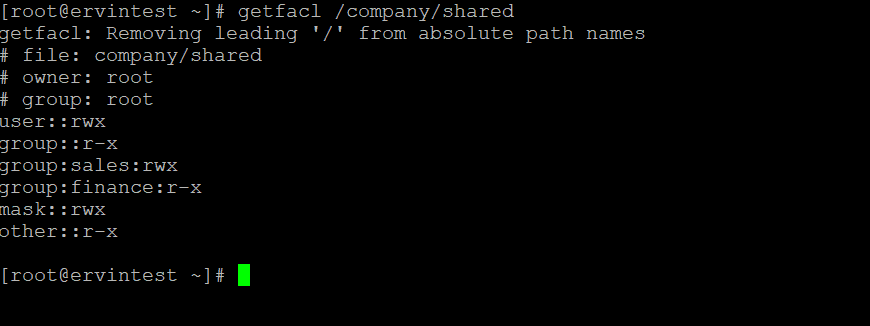
[root@ervintest ~]# getfacl /company/shared/sales_report.xlsx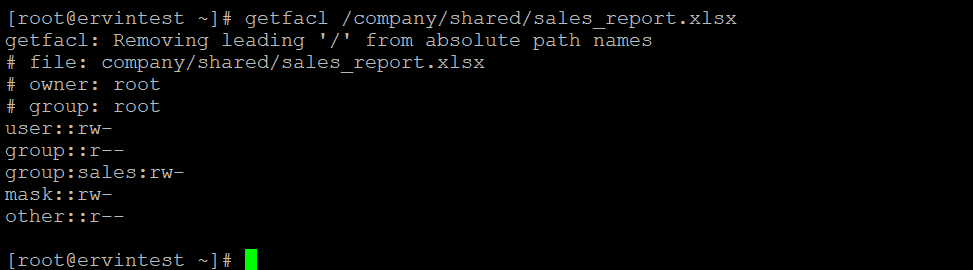
[root@ervintest ~]# getfacl /company/shared/financial_summary.pdf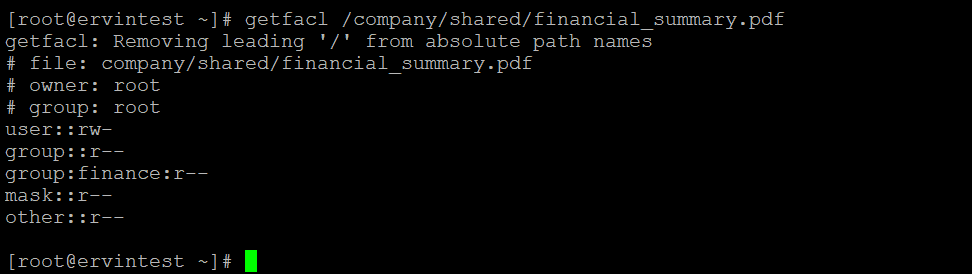
- Sales has read, write and execute access to the shared directory and read, write access to specific file(sales_report.xlsx)
- Finance has read and execute access to the entire directory, and read only access to financial_summary.pdf ensuring data integrity.
Certainly! Let’s consider another scenario where a user from the Sales group needs to set an ACL for a specific file within the shared directory /company/shared.
Suppose the user’s name is “alice” needs read and write permissions for a file named sales_presentation.ppt:
[root@ervintest ~]# setfacl -m u:alice:rw /company/shared/sales_presentation.pptTo confirm the intended ACLs
[root@ervintest ~]# getfacl /company/shared/sales_presentation.ppt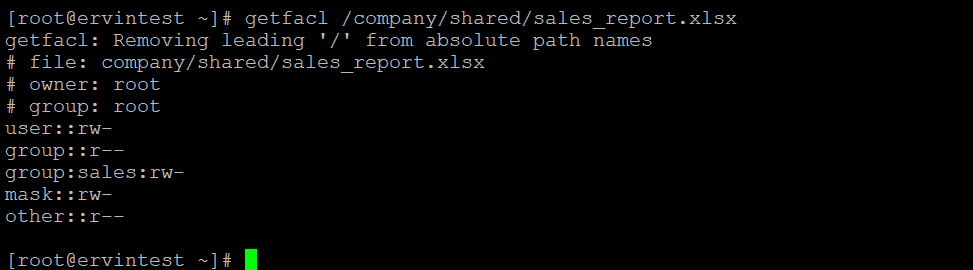
In this collaborative environment, ACLs proved invaluable in meeting the distinct needs of Sales and Finance. This fine-grained control ensures efficient collaboration while maintaining the security and integrity of sensitive financial data. Integrating ACLs into your system’s access management toolkit enhances your ability to tailor permissions, making it a valuable asset in diverse and collaborative work environments.
Removing Specific ACL Entries
- To remove an ACL entry, you can use the
-xoption with thesetfaclcommand. In the previous example, if you want to remove the ACL entry that grants read, write, and execute permissions to the “sales” group on/company/shared, you can use the following command:
[root@ervintest ~]# setfacl -x g:sales /company/sharedThis command removes the specified ACL entry for the “sales” group on the /company/shared directory. After running this command, if you check the ACL of the directory using getfacl /company/shared, you should see the updated ACL without the “sales” group entry:
- Certainly! If you want to remove all ACL entries for the “sales” group on the
/company/shareddirectory, you can use the-boption with thesetfaclcommand. Here’s the command:
[root@ervintest ~]# setfacl -b /company/shared
This command clears all ACL entries for the specified file or directory, effectively removing any ACL settings. After running this command, if you check the ACL of the directory using getfacl /company/shared, you should see that there are no ACL entries:
