
WordPress, after it was first released in 2003, has been storming on the internet. It has now become the most preferred CMS (content management system), powering around 75 million websites. With its rise in popularity WordPress also become a common target for hackers.
5 Common WordPress Security Issues
The following are the 5 most common WordPress security issues and ways to prevent them.

1. Cross-Site Scripting
Cross-Site Scripting (XSS) is a type of client-side injection attack. In this attack, the attacker does not primarily target the website instead, he/she uses it as a medium to attack the website users. At first, the attacker identifies a trusted website and then looks out for a potential XSS vulnerability in the website. A website is deemed to be XSS vulnerable if the code for user input or that to escape HTML tags are not written well. In this case, the attacker will be able to inject javascript into the search bar to steal the user cookies.

When hackers find this vulnerability in a site, they will inject malicious code or script to the site which can modify its actual content, or they may place links that redirect users to a dangerous website. Whenever an unaware visitor clicks on this link, a malicious code will be sent to their browser, which the browser accepts assuming it to be from a trusted site. The browser will either download the file containing the malicious code or else give the attacker access to its cookies. Once the attacker gets access to the victim’s cookies, he/she will be able to do unauthorised acts impersonating the victim.
How to avoid Cross-Site Scripting attack?
- Do sufficient input validation and make sure that the user enters the input in the correct format.
- Make sure to perform the appropriate input and output encoding.
- Follow the methods given in the Open Web Application Security Project’s (OWASP) XSS prevention cheat sheet for better security.
- Confirm the security of your website by performing penetration testing.
2. Brute Force Attack
Brute force attack is the simplest way of cracking the login credentials and encryption keys of a WordPress site. In this method, the hacker attempts all possible combinations of username and password, to force login to the website. The process is repeated until the right combination is found.
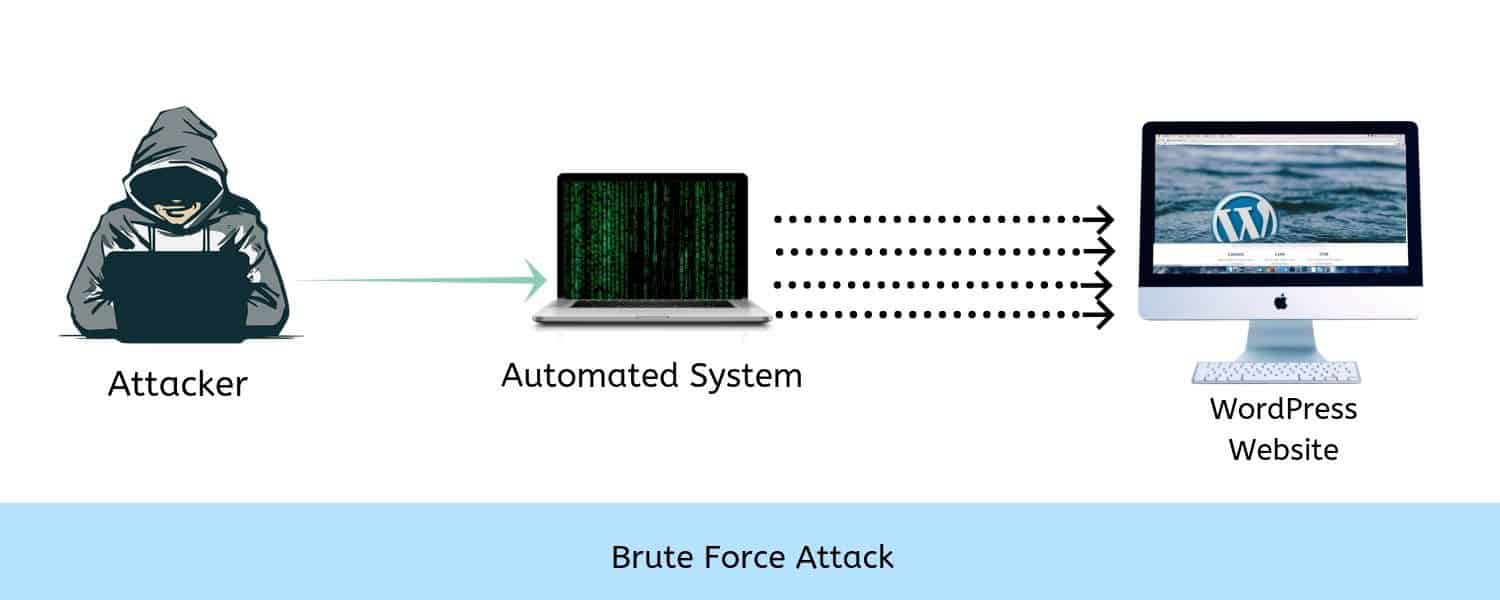
The attacker, however, doesn’t use any complicated techniques like decryption but uses a trial and error method to find the sequence. It is like, trying different keys in the keyring until you find the right one. Repeated guesses in a Brute force attack is executed with the help of automated tools. If the password tends to be longer then it will require a longer time to crack it, which can even go up to several weeks.
How to prevent Brute Force Attack?
- Increase the length and complexity of your WordPress login password.
- Include captcha verification to your website.
- Set a limit for the number of unsuccessful login attempts per IP address.
- Use a two-step authentication process to verify each user as they log in.
3. Distributed Denial of Service Attack (DDoS)
Before coming to Distributed Denial of Service (DDoS) attack, let us first discuss Denial of Service (DoS) attack.
A DoS attack is an attack where the attacker deliberately makes services unavailable to legitimate users, by overloading the server with meaningless connection requests. It can be related to the real-life situation where your mother puts away your mobile phone during your exam time. In that case, you will be denied all services from your mobile phone. All the traffic in a DoS attack comes from a single source, and so you can easily prevent it by blocking the IP address generating the traffic.

Distributed denial of service is an attack similar to DoS but on a much larger scale. Unlike that of a DoS attack, in a DDoS attack, the server will be attacked from multiple sources that are distributed around the world. The attacker initiates the attack by creating and distributing a malicious program over the internet. When an unguarded computer come across this program, it gets hijacked is recruited for a DDoS attack. An army full of such hijacked computers is called botnets or zombies. Zombies can be hundreds and thousands of computers spread all over the world. When an attacker commands them to attack, they start individually attacking the targeted server or network.
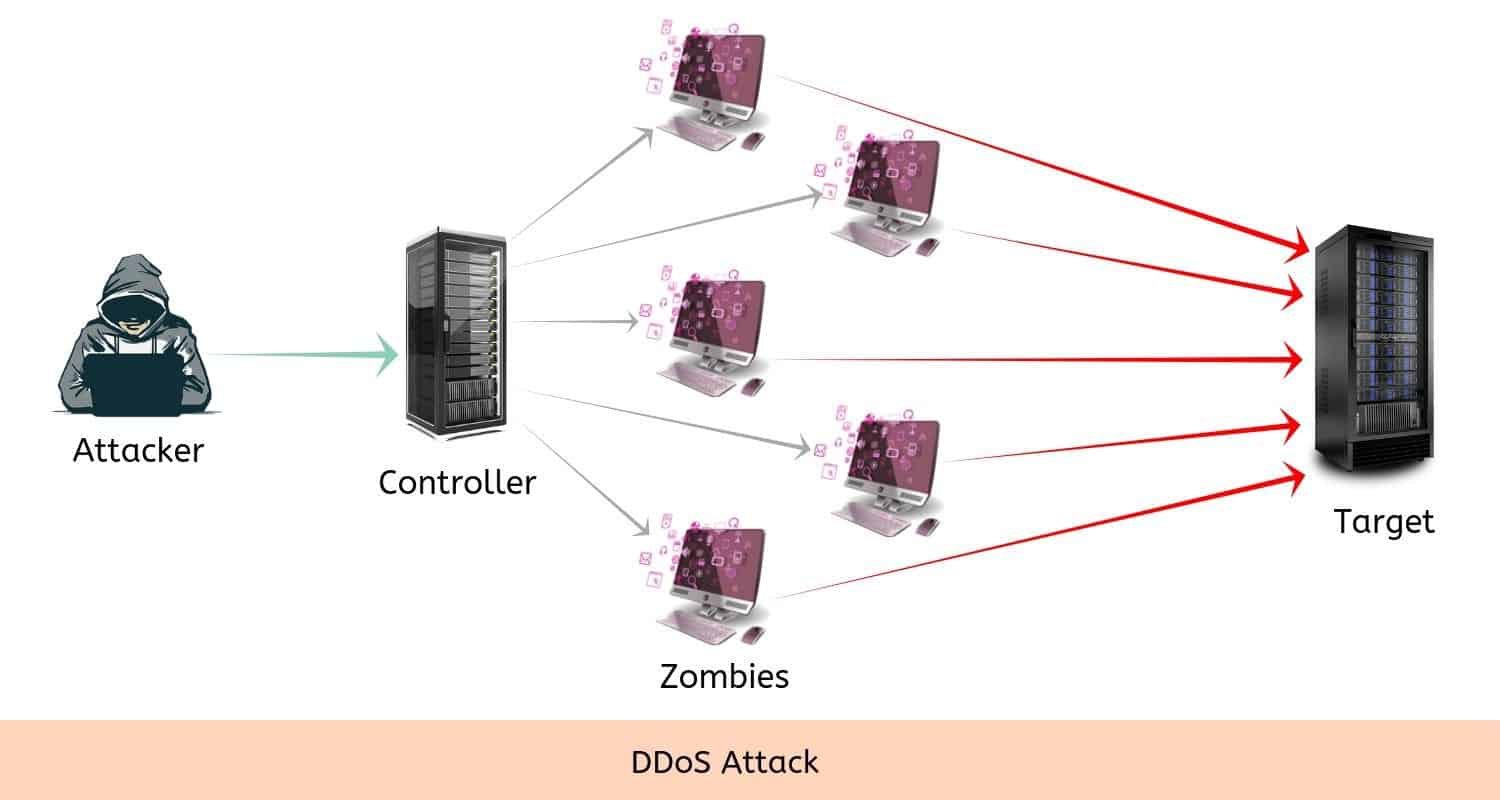
Methods to prevent DDoS Attack:
- It is always better to detect the attack at the earliest. For this, regularly monitor your WordPress website and look out for traffic spikes.
- Allocate more bandwidth to your site than it is required.
- Host your web server with a hosting provider as they may know more reliable tactics on dealing with a DDoS attack.
- Use the blackholing method, here the WebHost can direct the entire website traffic to a non-existent address if it is increasing uncontrollably.
4. SQL Injection Attack
SQL Injection attack is a server-side injection attack, where the attacker injects SQL queries as input and bypass the application layer security, to gain access over the website’s database. It is the second most common WordPress attack after Cross-Site Scripting.
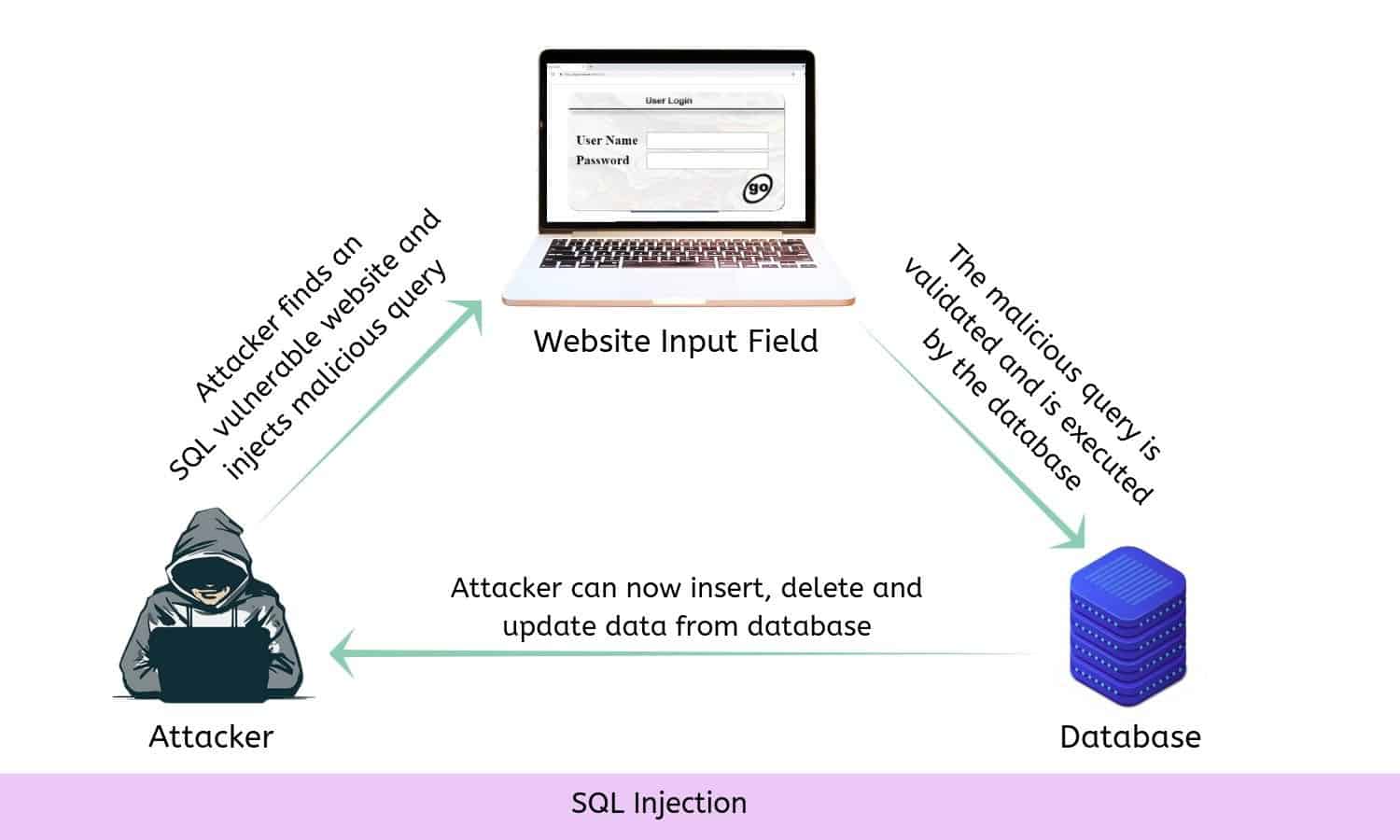
In an SQL injection attack, the attacker formerly finds an SQL vulnerable website and enters a malicious SQL statement along with the normal site request. The attacker then tricks the system into giving him/ her access to all data in the website’s database. The attacker will then be able to insert, delete, and update data from the database. That includes creating a new account, adding, deleting and altering records, adding and removing transactions etc. And, this may damage the entire database of the website. This type of attack mostly occurs due to vulnerabilities present in themes, plugins, core files, comment forms, custom coded sections or any other submittable input field.
5 steps to prevent SQL injection:
- Always keep your WordPress files, themes and plugins up to date.
- Make sure that the user input is always validated and sanitized.
- Encrypt all user details, including the login information and credit card details.
- Pre-compile the SQL statements using parameterized queries so that, it can be executed only by entering the parameters.
- Scale down the surface of attack by removing all unwanted functionalities from the database.
5. Malware Attack
Malware is a malicious program that takes advantage of vulnerabilities present in the website, to create disruption and steal sensitive information. Some of the commonly seen WordPress malware include backdoors, pharma hacks, drive-by download attack, and malicious redirects.
Ways to prevent Malware attack:
- Never download pirated themes or plugins only install themes and plugins from reliable sources.
- Use a different username other than admin for your website, as it is easier for hackers to guess this name.
- Always keep a backup of your WordPress files, themes, and plugins as it will help you to quickly recover your WordPress website if at all, it gets compromised.
- You can also compare your WordPress files with a copy of newly installed WordPress and remove all suspicious files. While doing this remember to keep a copy of the file to be deleted.
- Choose a better hosting provider. In Veeble, we perform regular malware scans and automatically quarantine the malicious software, if it is found.
With Veeble, host your WordPress website securely. Our 24*7 dedicated technical support team will ensure your site is running smoothly and without hitches day and night!
Also Read: How to Start A Blog with Veeble’s Managed WordPress Hosting


